All Logs Go To Heaven
It’s 9:00 PM. Do you know where your logs are? Hopefully in the cloud, far away from the grease smeared, Miller High-Life soaked fingers of the local datacenter sputz who is one brainzap away from disappearing your logs from existence.
Sending your logs to the cloud can be a solution if you don’t have the time or convenience of maintaining on premises infrastructure that can be costly and time consuming to maintain. Sending Windows event logs to a centralized store in the cloud provides benefits especially when it comes to monitoring endpoints that are frequently in disparate locations located outside of enterprise infrastructure. When it comes to handling information security incidents, we don’t always have the time and luxury for an endpoint to sign-on to VPN or phyiscally return to the enterprise network in order to get the vital telemetry that is necessary for us to identify who, what, and when something bad may have happened. We want all the important and valuable logs as often as we can afford and allow.
Your logs belong in a safe space, let’s get them there.

Sysmon 101
If you haven’t already, get Sysmon installed and going on your endpoints. I recommend this configuration as a solid baseline to build from.
Let’s Get Clouding
Once that’s up and running on an endpoint or two, let’s get to the cloudcity. Microsoft Azure provides us the ability to do this relatively painlessly. Start out by signing up for a free trial account if you don’t already have one. Meet back here once this is complete.
I’m more of a Google Cloud Platform guy myself but there’s no downside to being comfortable in multiple cloud environments and Microsoft provides some compelling offerings for affordable prices (free) when it comes to dealing with Windows endpoints. Oh, did I mention they provide an agent for forwarding Linux Syslog to the same centralized console? Tell me about it, Microsoft has some a hell of a long way from the 90’s…
The first 5Gb of logs ingested are free.
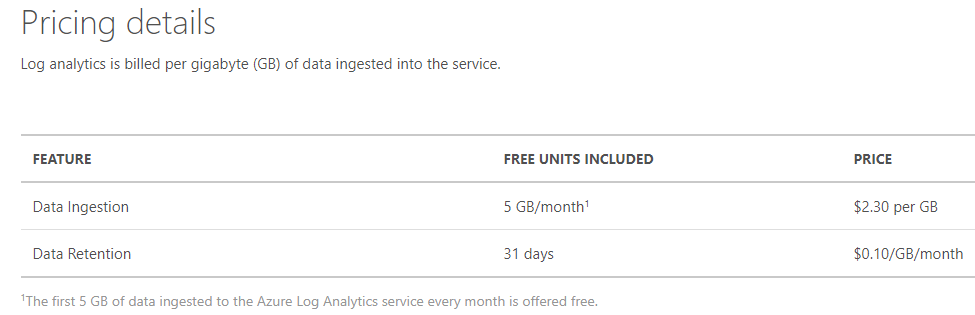
Microsoft provides documentation on downloading and installing the agents here. Once you’ve got your workspace ID and key entered in respectively, give it a few minutes and you should see a heartbeat from your endpoint appear in the monitoring console.
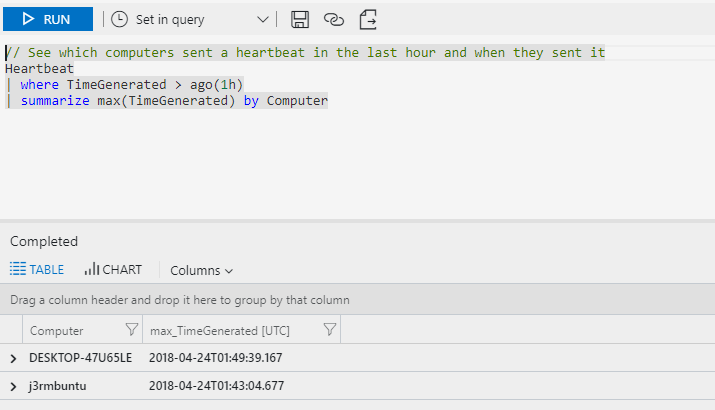
Free Sysmayne
Time to free the Sysmayne. So that’s great we’ve got heartbeats, but let’s get some sysmon rolling so we can actually see what’s going on.
In order to get sysmon logs flowing to the primary OMS console, it’s as simple as going back to the primary workspace and under Advanced Settings -> Data -> Windows Event Logs add Microsoft-Windows-Sysmon/Operational to the event logs to be collected. A drop-down won’t appear as you type is this is not a pre-defined log category at this point in time.
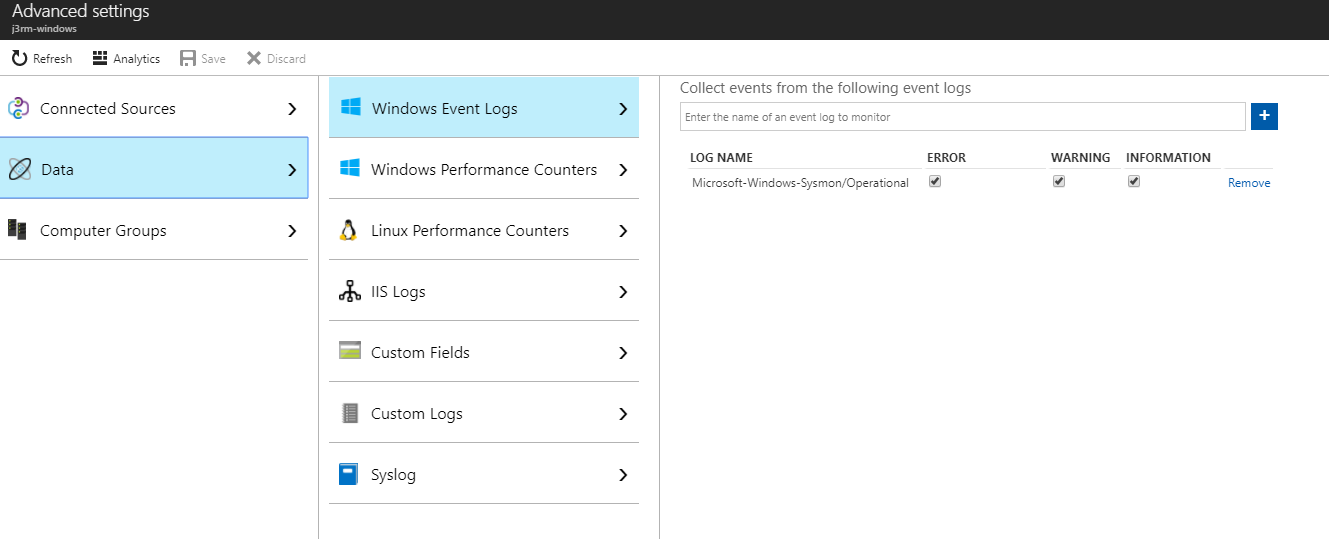
Now we can start digging through these logs from a *centralized, always available console that isn’t prey to the whims of our security engineers and their willingness to keep infrastructure running! Enjoy!
Let’s look at network connections (Sysmon event ID 3):
// See some sysmon goodness :)
Event
| where EventLog == "Microsoft-Windows-Sysmon/Operational"
|where EventID == 3
Results:
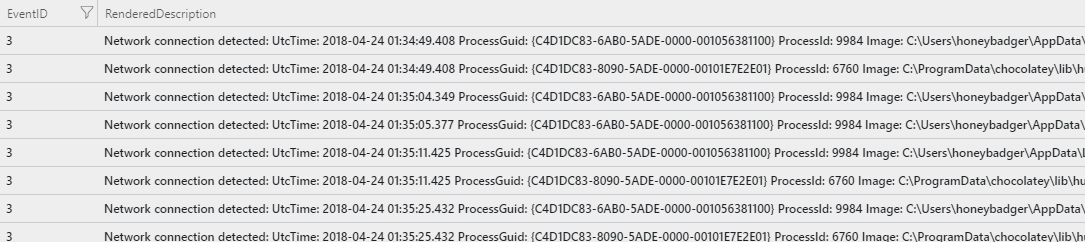
The logs need some parsing and cleaning up but it’s a good start and best of all it’s free for the first 5 GB. Hit me up on Twitter with feedback, thanks for your time and hope this helps to get folks started logging to the cloud.